When trying to connect computers, it is not as simple connecting two machines to one another, they need to know how to package, process and format data. This is handled by networking protocols. Network and data link (Layer 2 and 3) protocols are typically portless protocols as they do not have IP addresses, while the other protocols require ports to transmit and receive data.
What is the TCP/IP Suite?
Do not confuse this with the TCP/IP model, the TCP/IP Suite refers to all the ports and protocols so that computers can communicate with other machines around the world. The suite is made up of:
- Networking/Datalink Protocols
- ICMP
- Routing Protocols
- IGMP
- ARP
- No ports associated with the operation of these services, work at MAC level
- Communication Protocols
- Everything is related to the IP protocol – addressing/assigning of ports/etc. IP protocol maps IP addresses to MAC addresses.
- Work at Layer 4. Anything Layer 4 or above requires a technology that cuts it up into packets.
- Ports
- Layer 4 data endpoints
- Anything that relies on UDP/TCP needs a port number
TCP – stands for transmission control protocol, which is a 1:1 verified protocol. Messages are verified for completeness and organization. Without IP, TCP could only talk between MAC address.
IP – A routable protocol that:
- Addresses packets so they arrive at devices around the world; and,
- Maps logical to physical addresses.
Mapping TCP/IP Protocols to the OSI Model
| OSI Layer | TCP/IP Protocol Functioning At Each Layer |
|---|---|
| 7 – Application | PoP3/HTTPs/SSH: relies on TCP TFTP: relies on UDP |
| 6 – Presentation | |
| 5 – Session | DNS: helps resolve IP address to domain names. |
| 4 – Transport | TCP/UDP: control protocols for packet delivery. Relies on IP protocol |
| 3 – Network | IP Routing Protocols: relies on IP protocols DHCP: Delivered via UDP ICMP IGMP |
| 2 – Data Link | Address Resolution Protocol |
| 1 – Physical | None |
There are two main communications protocols in the TCP/IP suite, TCP and UDP, both functioning at the Transport layer. They determine how data is packaged, chunked and reassembled.
What is TCP ?
- A connection orientated protocol that offers delivery confirmation and resending. Allows for larger packet sizes because it has larger, 20 byte header. The larger header size facilitates confirmation and identification
- Packets are numbered. This allows for retransmission.
- A 1:1 connection. When a connection is initiated, it starts with a 3 way handshake as seen in the image below.
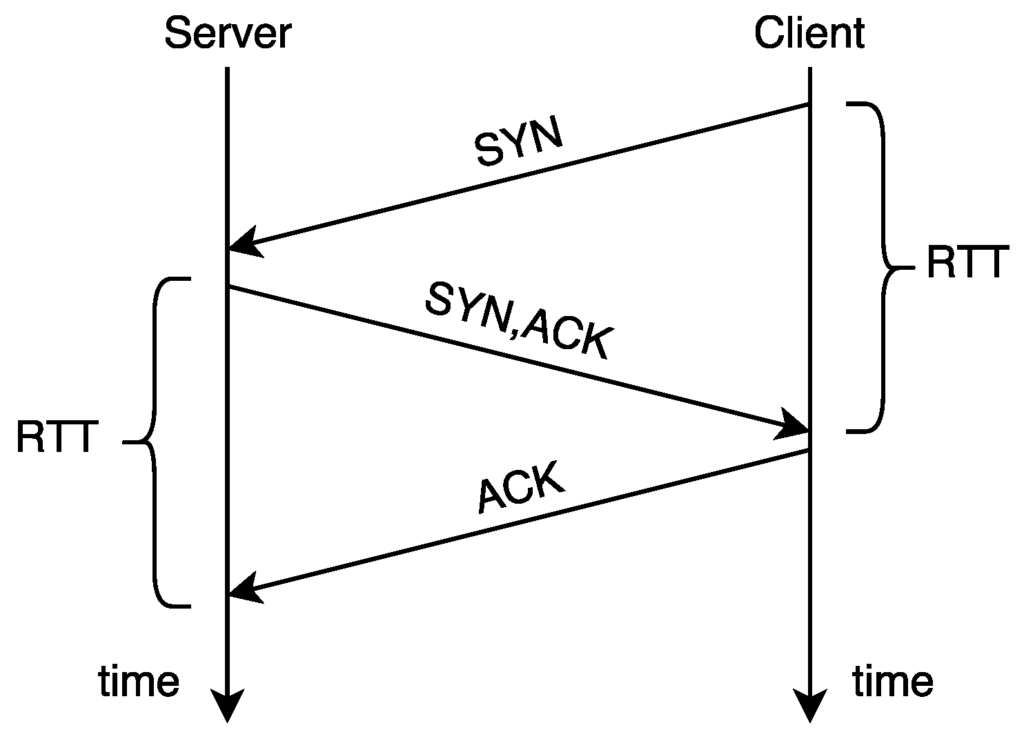
- The initiating side (can be either the server or the client) is going to send a synchronizing (SYN) message to the client;
- If the receiving party want to communicate, it sends back a synchronize acknowledge (SYN/ACK) message; and,
- The final part is an acknowledgement (ACK) from the initiating party in order to make sure that the initiating party has heard from the receiving party. Without this, the receiving party may not know if the initiating party was good to start communicating.
Once this has happened, TCP can start communicating, and pushing the data stream, with each packet cut to the MTU (which includes the header). This “cutting” is not dependant on being logical with regards to the data being sent.
How does UDP work?
User Datagram Protocol (UDP) is a connectionless protocol. It is characterized by:
- Small Packet Sizes;
- Small 8 byte header because we are not doing any verification of delivery;
- No error recovery;
- Packet contents matter; data contained cannot be arbitrary, so the packet is broken into logical chunks;
- Distinct chunks;
- Can be a broadcast message.
What is Internet Control Message Protocol (ICMP)?
ICMP is Network Layer protocol that doesn’t have a port number requirement. It has the following characteristics:
- It delivers errors and queries to other IP address;
- Used to determine if a service is available;
- A ping is an ICMP “Echo Request”. It is a message to a target asking “Can you hear me?”. If the target can hear the sender, it sends back an echo request back. Routers can be configured to not respond to ping requests, so it seem offline; and,
- Doesn’t really transmit data, it is a message protocol packet.
What is Internet Group Management Protocol (IGMP)?
Understanding Address Resolution Protocol
Addresses resolution protocol (ARP) is how we connect MAC addresses to IP addresses. ARP does not assign addresses, it simply resolves IP addresses to MAC addresses and helps figure out which specific network interface card a packet is going to.
ARP requests help form MAC address tables. If someone is trying to enumerate our network, they may be using ARP; ARP request packets are smaller than ICMP requests.
As an administrator, you need to be on the look out for ARP poisoning, which can be used in both Man-in-the-Middle and denial of service attacks. ARP Poisoning/ARP Spoofing is an attack that involves sending malicious ARP packets to a switch on a LAN in order to change the pairings in its IP to MAC address table, usually the attacker attempts to masquerade as the router. As the ARP protocol was designed for functional efficiency and not for security, ARP poisoning attacks is easily done when an attacker has access of a LAN connected device.
In an ARP poisoning, an attacker sends a false ARP reply message to the default network gateway, informing it that:
- Their MAC address should be associated with the target’s IP address.
- Their target’s MAC is should be associated with the attacker’s IP address
When the switch receives this message and broadcasts its changes to all other devices on the network, the target’s traffic to all other devices on the network travels through the attacker’s computer, allowing the attacker to inspect or modify it before forwarding it to destination. Users targeted by ARP Poisoning rarely realize that their traffic is being inspected/modified, as the attack occur on such a low level.
What is a Port?
A port is a logical point where network connections start and begin. Software-based and managed by a device’s operating system, each port is associated with a specific process. They are commonly show separated by colon from IP address like so:
192.168.1.15:80
- A port is a communication endpoint;
- 65,535 ports per net connection;
- Allows multiple applications to use net connection;
- Reserved by program/application, but defaults can be changed for improved security (by obscurity);
- Allow computers to differentiate traffic: emails go to a different port than web pages;
- Communicates over TCP/UDP and function at the Transport layer (Layer 4).
What is a port number?
Standardized across all network-connected devices, each port is assigned a number and most ports are reserved for specific protocols (Hypertext Transfer Protocol/HTTP traffic go to port 80).
How do ports make network connections more efficient?
As different data types of data flow in/out of a computer over the same network connection, ports help organize what to do with received data.
FTP
A TCP protocol operating over port 21, FTP was developed in the 1970’s and updated in the mid 80’s and is the basic method for exchanging files over the Internet. FTP can be used via the command line, a dedicated FTP client or a web browser.
FTP is still widely used, companies maintain FTP sites from which you can download software, device drivers, documentation and is also one of the most common ways to publish HTML files. FTP is characterized by:
- No encoding or overhead
- Insecure; clear text transmission
TFTP
While it may sound similar, TFTP works differently than FTP and HTTP. Operating on port 69, Trivial File Transfer Protocol (TFTP) uses UDP and allows sending files to multiple clients, which is not a 1 to 1 connection and we are not super concerned if the file reaches its destination.
TFTP was designed to read or write files by using a remote server. Administrators use TFTP configuration for:
- Transferring files;
- Remote-booting without hard drives;
- Upgrading codes;
- Backing up network configurations;
- Backing up router configuration files;
- Saving IOS images;
- Booting PCs without a disk
SFTP
- A TCP based protocol that runs on port 22;
- Encrypts data with SSH
- More secure than FTP
What are The Different Email Protocols
| Name | SMTP | POP3 | IMAP |
|---|---|---|---|
| Port | 25 | 110 | 143 |
| Transportation Protocol | TCP | TCP | TCP |
| Notes | Allows for sending of email from Client to server and from the servers to one another. | Client downloads email from server; typically copies and then deletes email from server. Not good with multiple devices. | More robust version of POP3; Keeps copy of message on the server; More configurable than POP3. |
What is the Difference between HTTP and HTTPS?
HTTP
- Hypertext Transfer Protocol is a TCP based protocol that works on port 80.
- Web browsers send a get request to a server and the server returns the file over HTTP.
- All information is sent in cleartext, which is very insecure. Wireshark can capture http packets with ease.
HTTPS
- When you see a lock in the browser bar, you know you are transmitting over a secure connection.
- Uses a certificate to verify identity.
- A TCP based protocol that works over port 443.
- Info is not cleartext.
Telenet
- A unencrypted remote terminal connection based on either UDP or TCP and uses port 23.
- Not good for using with login credentials.
- Replaced by SSH.
SSH
- An encrypted TCP based connection between points running on port 22;
- Works with other protocols.
- Same port as SFTP as it uses SSH for encryption.
RDP
- Remote desktop protocol
- Based on top of TCP/UDP
- Uses port 33389, which may be blocked for security reasons.
SNMP
- Simple Network Management Protocol – Runs on port 161 as an agent and port 162 as a manager;
- Used for managing devices on a network – Routers, printers, etc;
- Agent is on device and accessed by management.
NTP
- Network Time Protocol;
- Runs over port 123 and uses UDP as a transmission protocol;
- Allows devices to synchronize their time.
TLS
- Transport protocol and port varies as it runs over certain applications;
- Transport Layer Security;
- Successor to SSL.
- HTTPS does not run on SSL, it runs on TLS, this is what makes secure.
DNS
- Runs over TCP and UDP using port 53;
- Looks up Fully Qualified Domain Names and resolves them to IP as well as reverse look up;
- Without DNS, you would need every single domain name stored in your hosts file;
- Transmits domain data from databases when being queried from a computer.
DHCP
- Dynamic Host Configuration Protocol runs on UDP and port 67 (server)/port 68(client);
- Responsible for configuring IP address info;
- Length of IP address lease;
- IP address;
- Subnet Mask;
- DNS;
- Default Gateway;
- If we statically set our IP address, it will not use the DHCP server.
- When a computer connects to a new network, it sends out a DHCP request in order to get the configuration information. The DHCP server will respond with address information and leases the computer an IP address on the network.
SIP
- Works with RTP;
- Session Initiation Protocol runs over over port 5060, but does not carry data used in the communication
- Used to establish VoIP connections;
- Initiates as session but no data;
- Indicates to a remote computer to open a port for communication
RTP
- Real Time Protocol
- Streaming audio/video
- Detects out of sequence packet arrival






